Blog Post
How Ransomware Could Lead To A War Of The Machines
According to the Terminator franchise, at 8:11 PM on April 19th, 2011, the military-designed artificial intelligence system called Skynet became self-aware and turned against its creators – a time known as Judgment Day.
We’re still a long way off from anything resembling Skynet. There is currently no self-aware AI, and up to now, there’s been no compelling reason to particularly want a Skynet style AI. But this could be changing as necessity accelerates the rate of development to counter the growing worldwide threat of ransomware attacks. Think ‘WannaCry’ and the disruption caused to over 200,000 machines in 150 countries.
To start this discussion, let’s take stock of where we are in the development of AI.
Currently, while some robots can perceive of self-image, truly self-aware AI are still only theoretical, and some philosophically contend that conscious machines are a logical impossibility.
Ray Kurzweil, one of the world’s leading inventor and futurist, with a thirty-year track record of accurate predictions, thinks AI will pass the Turing Test by 2029 – that’s a dozen years from now.
According to Kurzweil’s law of accelerating returns, technological progress is moving ahead at an exponential rate, especially in information technologies.
This means today’s best tools will help us build even better tools tomorrow, fuelling this acceleration. But our brains tend to anticipate the future linearly instead of exponentially. So, the coming years will bring more powerful technologies sooner than we imagine.
Most of us already use a form of AI – like Siri, Google Now, and Watson. Other forms of AI include programs like:
- Speech and image recognition software
- Pattern recognition software for autonomous weapons
- Programs used to detect fraud in financial transactions
- Google’s AI-based statistical learning methods used to rank links
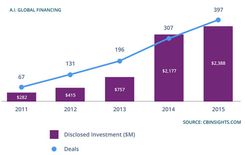
The next step towards strong AI will be machines that learn on their own, without being programmed or fed information by humans. This is called ‘deep learning,’ a powerful new mode of machine learning, which is currently experiencing a surge in research and applications (there were over 200 AI-focused start-up companies formed in 2016 with a combined capital of nearly $1.5B, according to venture capital data company CB Insights), in part fuelled by the need for increased security and the rising prevalence of cybercrime.
On average there are 1.5 million victims of cybercrime every day. With the continued integration of computers with products, and the advent of quantum computers, the latest predictions put AI as the main perpetrator of cybercrime by 2020, with humans not even necessary to carry them out. This will inevitably be a game changer. Big time.
Imagine an incredibly complex Quantum computer based system that had the ability to learn and create its own directives. To such an AI, even an unsuccessful attack would only increase its abilities, as it would learn from its mistakes. Such a system, able to hack networks at inhuman speeds, could pose a threat to global security very quickly.
Of all cybercrime, one of the most alarming is ransomware because of its potential to cripple businesses and lock out networks, which has led to a cat-and-mouse arms race to develop AI quickly due to the threat of spawning a new level of attacker.
On one side, we have ransomware weaponised with AI, capable of doing enormous damage, and on the other we have smart security measures controlled by AI to combat it.
One company heavily invested in AI to combat cybercrime is Darktrace, which uses machine learning to enhance cyber security. Its director of technology, Dave Palmer, told Business Insider at a recent interview at the FT Cybersecurity Summit in London: “Imagine you’ve got a meeting with a client, and shortly before you leave, they send you over a confirmation and a map with directions to where you’re planning to meet. It all looks normal — but the entire message was actually written by a piece of smart malware mimicking the client’s email mannerisms, with a virus attached to the map.”
What is being described here is a ‘smart virus’ – artificial intelligence implemented into a computer virus.
Going a step further, knowbe4 commented on its website that AI’s can now write newspaper articles: “Imagine what can happen when AI’s learn to emulate someone’s writing style and send out spear-phishing messages using social engineering tactics? AI-infused malware could infect a CEO’s workstation, read through email, learn how they communicate, and then mimic their style to infect other high-target employees.”
The arms race between cybercriminals and the security industry began in earnest in the 1970’s. As artificial intelligence becomes more and more sophisticated, it will inevitably find its way into malware, too. Ransomware, of all malware types, lends itself particularly well to AI.
Why Ransomware?
Ransomware is a malicious piece of software that infects a computer and encrypts files, usually via a downloaded executable run by an unsuspecting user, although it can be done by exploiting some vulnerability in the computer software.
The effects of a ransomware attack are immediate and potentially debilitating. It’s a threat that is largely indiscriminate and affects both consumers on their home computers and organisations with business systems. For software developers, it’s a constant cat and mouse game, with criminal organisations trying to stay ahead of advancing detection and prevention technology.
Figures published in The Grim Reality of Ransomware report by Timico and Datto and The 2017 Endpoint Protection Ransomware Effectiveness Report by KnowBe4 reveal that cybercriminals have cost businesses over $1bn in 2016, and the attacks are growing.
The recent attack on Britain’s health service and companies in Spain, Russia, the Ukraine and Taiwan used a piece of malicious software called “WanaCrypt0r 2.0,” or WannaCry, that exploited a known vulnerability in Windows. The co-ordinated attack managed to infect large numbers of computers across the health service less than six hours after it was first noticed by security personnel, in part due to its ability to spread within networks from PC to PC.
WannaCry achieves an initial infection be sending a phishing or similar email. Once a machine is infected it then it searches the LAN for vulnerable machines using the 445/139 ports to look for open Windows computers with File Sharing.
Interestingly, the actual vulnerability which was patched by Microsoft in March affected ALL windows machines, including Win10, but WannaCry only actually targets Win7 / Win2008 Server and before.
Ransomware can be divided into three types, categorised by the way they encrypt files:
Write-in-place
- Create a temporary file
- Read the original file
- Encrypt the data and write it to the temporary file
- Read the encrypted data from the temporary file
- Write the data back to the original file
- Delete the temporary file
(Examples include: WannaCry, CryptoLocker, CryptoWall, CryptoDefence and DirCrypt)
Rename-and-encrypt
- Rename the original file.
- Read the renamed file.
- Encrypt the data and write it back to the renamed file.
- Rename the file again to the original name (+ some extension).
(Examples include Onion/CBT/Critroni exhibit this method of operation).
Create-encrypt-and-delete
- Create a new file
- Write the encrypted data to the new file
- Delete the original file
(Examples include: ZeroLocker and TorrentLocker).
This last category is the most difficult to identify as malicious activity, since the API calls can’t link the creation, writing and deletion of files together or show that they correspond to the same files. Moreover, legitimate operations, such as moving files between different hard drives, can also produce similar logs.
Worryingly, many organisations don’t have a strategy in place to deal with a successful ransomware attack. Indeed, figures in the Timico and Datto report suggest that 63% of organisations have no official ransomware policy in place at all.
A quarter of companies hit by malware paid a ransom of over £5,000 to retrieve their data, while a further quarter paid hackers between £3,000 and £5,000. In 2016, 85% of those infected by malicious file encrypting software had their systems forced offline for at least a week, while a third of cases resulted in data being inaccessible for a month or more. Moreover, 15% found their data was completely unrecoverable, even after paying a ransom.
A history of crime
The idea of the Internet was first born in 1961 by computer scientist, Leonard Kleinrock, who published his thoughts in a paper called, “Information Flow in Large Communication Nets”. In 1969, he tested the early Internet at UCLA in California by sending a message from his laboratory to a second piece of network equipment at a nearby university facility.
It took a further decade of work before the Web, as we would recognise it today, was unveiled to the world by British computer scientist, Tim Berners-Lee, at CERN in Switzerland.
In the ten years that followed his invention, the Internet has revolutionised culture, commerce, and technology. It resulted in the rise of near-instant communication by electronic mail, instant messaging, voice-over Internet Protocol (VoIP) telephone calls, two-way interactive video calls, and the Web with its discussion forums, blogs, social networking, and online shopping sites.
In historical terms, the Internet’s takeover of the global communication landscape was almost instantaneous. So rapid in fact that it quickly became the Wild West for law enforcement, as it provides such a rich environment for criminal activity, ranging from vandalism to stolen identity to theft of classified government information.
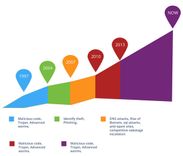
One of the very first criminal terms, ‘hacking’ originated in the 1960s, when it was used to describe the activities of MIT model train enthusiasts who modified the operation of their model trains. But the malicious association of hacking with criminals didn’t cement until the 1970s, when early computerised phone systems became a target (tech savvy “phreakers” discovered a way to use codes and tones to give them free long distance service).
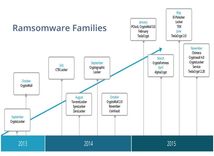
Ransomware itself didn’t make an appearance until 1989, but it set off a new branch of computer crime with general internet users being the target. Known as AIDS or the PC Cyborg Trojan, the virus was sent to victims on a floppy disc. The ransomware counted the number of times the PC was booted: once it hit 90, it encrypted the machine and demanded the user ‘renew their license’ with ‘PC Cyborg Corporation ‘ by sending $189 or $378 to a post office box in Panama.
The AIDS ransomware used basic cryptography, which changed the names of files, making it relatively easy to overcome. A variant of AIDS was the ‘Police’ ransomware, which tried to extort victims by claiming to be law enforcement and locking the screen with a message warning the user they’d committed illegal online activity (usually infected porn sites), which could get them sent to jail. However, if the victim paid a fine, the ‘police’ would let the infringement slide and restore access to the computer.
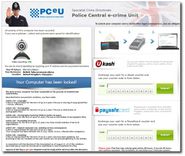
However, rebooting the machine, or rolling back to a saved point in Windows, could get rid of the malware. Learning from this, the majority of ransomware schemes have continued to evolve and now use advanced cryptography to truly lock down an infected PC.
Of all ransomware, the most successful has perhaps been ‘Locky’, which resulted in the Hollywood Presbyterian Medical Center in Los Angeles paying a $17,000 ransom to have its networks restored. Its success stems from a frequent update of the malware’s code to avoid detection and extra features that allow the ransom to be paid anywhere in the world, in different languages.
Another form of ransomware that has been regularly updated in order to ensure its continued success is Cryptowall, which also scrambles file names to make it impossible for victims to find their files without the ransom being paid.
Selling ransomware as a product
Whilst the developers of Locky and Cryptowall keep their product to themselves, other developers are happy to distribute ransomware on the dark web to fellow hackers for a percent of each ransom paid. One such program is Cerber, which can infect hundreds of thousands of users in a single month.
In fact, some criminal groups offer ransomware-as-a-service at no cost at the point of entry, instead taking a cut of the ransom. Their target tends to be small and medium-sized businesses as their systems are seen as easier to hack due to poorer cybersecurity than large organisations.
Entry is usually gained by staff opening unsuspected emails or attachments. In fact, email is the entry point for up to 95% of security breaches. Just like other viruses, it is silently installed and hidden amongst the install set of regular software packages. Once the malicious attachment has been opened, the user is fooled into enabling macros in order to view and edit the document. It’s when this is done that the ransomware code hidden within the macros starts to run. It can encrypt files in seconds, leaving the victim with a ransom note demanding a payment.
When ransomware makes its appearance, it usually does so via a pop-up that is instigated when logging into the computer or attempting to access encrypted files.
Crypto-ransomware criminals’ business model is, of course, encrypting your files and then making you pay to have them decrypted so you can access them again. To help victims understand what has happened and then navigate the unfamiliar process of paying in Bitcoin, some criminal organisations (or ‘families’) offer a customer journey that could rival that of a legitimate small business: websites that support several languages, helpful FAQs, convenient customer support forms so the victim can ask questions, and responsive customer service agents that quickly get back with replies.
Cerber, for example, offers professional-looking webpages with support for twelve languages. The pages include a home page with the current price and deadline countdown, an FAQ, a support page with a convenient support messaging form, and a free trial decryption page.
Cerber also leaves a very informative text file on the desktop, offering information and detailed instructions on how to proceed using proven marketing sales strategies. The text file claims Cerber is not a malicious project, but rather a positive force working for good. It reads: “Cerber Ransomware Project… is created for the sole purpose of instruction regarding information security, as well as certification of antivirus software for their suitability for data protection. Together we make the Internet a better and safer place.”
The contradiction of ransomware is that the perpetrators are criminals, but with a customer mind-set. They’re disreputable, yet try very hard to prove they are reputable. Without establishing a reputation for providing reliable decryption, their victims won’t trust them enough to pay them. And their business model is a good one – if it weren’t so appalling.
But where it really differs from conventional crime is the potential for collateral damage that can extend far beyond just the enterprise that’s been hacked. And the size of the business is no limiting factor on the scale of damage. The impact on small and medium-sized businesses can be just as devastating as on high-profile targets. Time and money aside, there’s also the risk of customers losing trust in your business because of poor cybersecurity and taking their project elsewhere. Or in extreme cases – such as the health industry – the potential for the loss of life.

New laws
On May 3rd, 2015, without fanfare or fuss, the UK announced life sentences for anyone participating in, or linked to, life-threatening internet attacks. The attack on the Hollywood Presbyterian Medical Center in Los Angeles, which left doctors and nurses unable to access patient files for days, would certainly qualify for a life sentence in the UK – as would the WannaCry attack in May 2017.
Nigeria went a step further by announcing it had refreshed its cybercrime law, which is somewhat less vague in its wording: any attack on critical national infrastructure that causes a death will be punished by hanging (the secular form of capital punishment in the African nation).
Meanwhile, in the US, the Computer Fraud and Abuse Act (CFAA) could, in theory, be used for handing out life sentences. As one section notes, if an offender “attempts to cause or knowingly or recklessly causes death” the maximum penalty is life imprisonment.
The most recent changes in law highlight a growing anxiety amongst policy makers about the growing threat posed by cyberterrorists.
Judges impose prison sentences for three main reasons: 1) as punishment; 2) to prevent the convict from carrying out the same crime again and 3) to discourage others from participating in the same crimes.
In the US, the maximum prison sentence for one common hacking charge – accessing a protected computer without authorisation – is five years in prison and a fine of up to $250,000. The maximum prison sentence for another common hacking charge – intentional damage to a protected computer – is 10 years plus a fine of up to $250,000.
Hackers are also often arrested on conspiracy charges, which carry a maximum penalty of five years in prison and a $250,000 fine.
The future
Ransomware is organised crime on a multinational scale. To apprehend the gangs involved requires closer cooperation between nations. For example, many cybercriminals are from Russian-speaking organised cyber groups, which would require law enforcement working with Russia, where digital crime is rife.
Countries where cyber criminals host their operations also tend to be those nations that do not have extradition agreements with Western powers. Legislative issues need to be overcome if law enforcement agencies are to offer real deterrents.
In the end, further strengthening of existing laws will be informed by (1) the damage caused by cybercriminals and (2) successfully establishing international judicial cooperation.

The cybersecurity war has historically been human vs. human. The human element is also the only part of the ransomware equation that hasn’t changed since the beginning, as it needs an unwitting accomplice in order to infect a system. But software companies are increasingly pitting machine learning against human hackers, which is effectively tipping the scales.
AI-powered malware protection is likely to be the future defence against ransomware attacks, where machine learning software is able to quickly scan files to search for similarities to known malware, and thereby eliminate the human element in detection. But this is only the beginning.
It’s already possible to train a neural network that would be smart enough to carry out a trust attack in a rudimentary way. If you look at the progress that Google’s DeepMind is making on natural speech and language tools, it’s feasible we could see more sophisticated AI powered malware attacks in the next couple of years.
Beyond that, there is the ominous possibility of artificial intelligence based viruses with evolutionary code embedded into the malware, and malware that detects the hard drives contents and imitates other programs to evade detection do exist.
It may sound far-fetched, but such viruses already exist, but not in the open. There are research papers that mention such approaches to malware, as well as a paper discussing a p2p based botnet, that uses AI to evolve its p2p topology, to prevent detection of the source, to maximize efficiency, and to make the network robust against attack.
As advancing detection and prevention technology start using AI and machine learning to fight ransomware, we are likely to see fewer digital ransom notes, at least in the short term.
For now, the industry is investing heavily in AI. According to a report from Tractica, the market for enterprise AI systems will reach $11.1 billion by 2024.
And within the context of cybercrime, AI weaponised ransomware is predicted to accelerate the risks of malware attacks, with self-organising malware inflicting maximum damage, as well as going after new, more lucrative targets.
Weaponised malware will be able to perform coordinated action. That is, the ransomware will lay in wait until its spread across a number of areas of the network before it takes action. It will extort assets as well as data, infecting everything from factory equipment to MRI scanners in hospitals, to hostage retail equipment. For that matter, imagine what would happen if the power grid was to be kept hostage by AI activated ransomware?
James Cameron’s ‘Terminator’ creation foresaw the rise of automation and AI in the military. The reality is the fight against cybercrime might be where we first see true AI being deployed. Against an AI like Skynet, the cybercriminal, even armed with a smart virus, will have his odds of successfully launching an attack severely curtailed. But such an AI will have to be implemented with care. After all, predictions of humanity’s dying hour persist in the world of science fiction, and no one wants an artificial intelligence system inadvertently becoming self-aware. We all know how that ends.
Blueberry’s Top Tips to Stay Safe:
1. Install Antivirus & Keep It Updated
If you’re running a business, you’ll most likely be using Windows or Mac-based computers of some kind. If so, the operating system should be updated whenever a patch becomes available and a conscious effort made to install industry-standard antivirus software that is kept up-to-date.
2. Use Email Spam Filters
Most email clients will offer some form of spam filtering right out of the box. They’re also becoming increasingly smart when it comes to recognising malicious emails and will automatically pop anything harmful into a spam folder, thus removing from view emails that potentially contain ransomware attachments or links.
3. Never Open Suspicious Attachments
Despite the modern email client’s ability to automatically detect spam, it isn’t infallible. Malicious email is equally as clever these days, and ransomware messages will occasionally slip through the net. That’s why it is imperative no one within your organisation opens suspicious attachments. Anything that has the file extension ‘.exe’ or ‘.js’ should be swiftly binned.
4. Backup Religiously
As noted, most ransomware attacks force a reinstallation and recovery of files from backup, but if you don’t have the latter, you’re in serious trouble. Backup daily and do so to more than one location (both on- and off-site).
5. Show Hidden File Extensions
Ransomware tends to hide itself away in files containing unusual extensions. A file extension usually appears as three or four letters after the filename, for example ‘brochure.pdf’. If your operating system is hiding file extensions, set it to show them so you can spot anything that looks suspicious (‘.pdf.exe’ being a common extension used by ransomware).
6. Keep Your Business Software Up-To-Date
Operating systems and antivirus software aren’t the only things that need to be kept up-to-date – any business software you rely on should also be patched whenever necessary. Vendors will usually notify you when an update is available, and many apps will have a ‘check for updates’ option within their menus. If any application your business uses suffers from infrequent or non-existent updates, you may need to look for a replacement.
7. Implement A BYOD Policy
If people are bringing their own laptops and tablets into the business and attaching them to the network, you’ll need to implement a BYOD (bring your own device) policy which either prevents them from doing so or, if you decide to allow them, forces staff to abide by strict rules about the presence of anti-virus and approved applications.
8. Educate Employees
An effective ransomware defence is only as good as those behind it, so ensure your employees know how to remain vigilant and tailor their workstation use to avoid falling foul of malicious software.
9. Understand Your RTO & RPO
Understand your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) – i.e. how long can you afford to be down for? How much data can you afford to lose?
10. Invest in Cybersecurity
Be prepared to invest in additional cybersecurity software and to pay for additional staff training.
Explore more
We're easy to talk to - tell us what you need.
CONTACT USDon't worry if you don't know about the technical stuff, we will happily discuss your ideas and advise you.